what policies should be in place to help reduce risk of cybercrime?
We'll walk you through how to cyber police force your data for cybercrime prevention and control
Many cyber security articles on cybercrime oft first with a shocking statistic about how cyber attacks are on the rise. Danger! Beware!
But we're not going to practice that here. Instead, nosotros're going to present you with parodied lyrics to a song. The evolving modern cybercrime landscape is suitable for a parody of an 80s song past The Constabulary:
Every account you create
Every transaction y'all make
Every security best practice you fake
Every e-mail you communicate
Hackers are watching you lot.
Information technology is true that cybercrime is increasing in occurrence each mean solar day and evolving to become more complex. But what is cybercrime? What constitutes such a significant (and growing) industry? In the broadest sense, cybercrime is any type of illegal action involving the internet. Some of the virtually common types of cybercrime include identity theft and information misuse, data and intellectual property theft, human being trafficking, child pornography, and terrorism. As you might guess from our variation of vocal lyrics, many of these crimes are committed using a variety of cyber security attack tactics such as phishing, CEO fraud, man-in-the-eye (MitM), hacking, SQL injections, DDoS, and malware attacks. Historically, these crimes were committed by alone wolves. Present, all the same, cybercrime is a booming industry comprised of criminal enterprises, organized hacker syndicates, hacktivists, and nation-country actors.
The gargantuan task of knowing how to prevent cybercrime frequently comes down to nullifying cyber security threats and figuring out how to forbid cyber attacks. Nevertheless, hackers' continuously-irresolute tactics, a growing number of actors, and rapidly expanding technologies make it challenging for cyber security experts and businesses alike to stay a minimum of one pace alee of cybercriminals. Furthermore, there is no one singular method of 100% cyber crime prevention — understanding how to prevent cybercrime is about bringing together an constructive combination of technologies, best practices, and procedures to craft the solution that is all-time for your business organisation.
What are some of the best methods cybercrime prevention and control from a business perspective? Permit'due south hash information technology out.
How to forestall cybercrime — step #ane: Follow manufacture best practices and guidelines
Cyber law-breaking prevention is not a one-size-fits-all approach. Organizations of unlike sizes have unlike needs, threats, risk tolerances, vulnerabilities, and capabilities. Luckily, governments, regulators, and fifty-fifty industry organizations accept provided some general frameworks and security recommended practices for organizations to follow to reduce their likelihood of falling victim to cyber security attacks. Nevertheless, information technology is important to note that some are more than particular than others in their recommendations or requirements. For example:
- GDPR, which stands for Full general Information Protection Regulation, is comprehensive legislation that rolled out in 2022 to protect the information and privacy of European Union citizens (even those living abroad and international companies that handle data of EU citizens). The regulation outlines much of what is or is not allowed, states what falls under data subjects' (the citizens') expectations of privacy, and details some of the potent penalties that businesses and organizations alike could face for noncompliance.
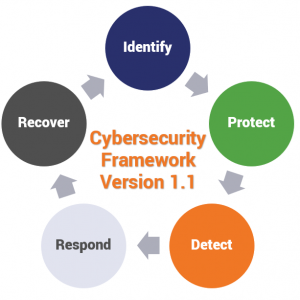
- NIST, also known equally the U.Due south. Commerce Department's National Institute of Standards and Technology, is the go-to resource for cyber security professionals. Last year, NIST released version 1.1 of its popular Cybersecurity Framework document, which outlines ways to improve cyber security for disquisitional infrastructure. The goal of the certificate is to provide "a prioritized, flexible, repeatable, performance-based, and cost-constructive arroyo, including information security measures and controls that may be voluntarily adopted past owners and operators of critical infrastructure to aid them identify, appraise, and manage cyber risks." Ideally, the framework should exist used to complement your organisation's existing cyber security program and risk management processes, not replace them, and outlines five concurrent and continuous "functions"— Identify, Protect, Detect, Respond, and Recover — to address cyber security risks.
- HIPAA, the national Health Insurance Portability and Accountability Human activity in the The states, is not every bit particular nor stringent as the GDPR most how patient data and confidential personal health records are to exist used, stored, or transferred. HIPAA'south Security Rule does not technically require encryption of patient health information (PHI). Instead, § 164.312's standard for transmission security says that organizations must "Implement technical security measures to guard confronting unauthorized access to electronic protected health information that is being transmitted over an electronic communications network." Even the rule's technical safeguards concerning the topic of encryption are defined simply as "addressable" requirements — handlers of PHI must "Implement a mechanism to encrypt electronic protected wellness information whenever accounted advisable." Isn't that comforting? Granted, the linguistic communication is left purposefully vague to account for development and changes in technologies. However, information technology also leaves businesses with potential opportunities to debate away their style out of responsibility and accountability.
- PCI SSC, the Payment Bill of fare Industry Security Standards Council, requires businesses that use business relationship data to implement certain protections for that information. These data security requirements, known as the PCI Security Standards, require encrypted transmission of cardholder data across public and open networks, use of strong access command measures, implementation of a vulnerability management plan, and more. Failure to comply with these standards can result in pregnant fines and penalties — not to mention possible suspension of your company'due south card payment processing capabilities.
Sounds elementary plenty, right? These are highly-regarded resource for IT security professionals and businesses alike. The trouble is, though, not all businesses adhere to these recommendations (or, in some cases, required practices). An concerning analogy is when an adult tells a pocket-size child not to touch a hot stove because they will get hurt, withal the kids does it anyhow: Some children (or businesses, in this case) cull to learn the hard manner and wind up getting burned. For companies who instead cull to "listen to the adult" and adopt these required or recommended methods of cyber crime prevention, they will be in a meliorate position to protect their data, employees, and customers from cyber security attacks and data breaches.
These other methods of cyber criminal offense prevention tin can (and should) include the following:
How to prevent cybercrime — step #2: Implement digital & physical security methods
Nosotros have previously discussed the thought of using firewalls, antivirus, network and server monitoring, and other forms of concrete and digital data center security measures to create barriers for cybercriminals. Aside from hacktivists and nation-state actors who are trying to attain ideal or political goals, many mod cybercriminals are simply looking for a fashion to make money. This could exist through wire transfer scams or by stealing business relationship information, personal data, or even intellectual property and proprietary research.
Nevertheless, the more challenging your defenses are to get through and the more than responsive you are to their attacks, the more work a hacker volition accept to do to attain their goals. This makes your business less appealing as a target. After all, why would a thief desire to become to the trouble and planning to rob a castle when they can just attack the king's wagon instead? This same approach tin can be said for hackers when they are choosing a target for a cyber security attack. In role, cyber crime prevention includes hardening your defenses equally much as possible and then that your visitor appears to be more problem and effort than the potential payoff is worth.
How to prevent cybercrime — footstep #iii: Maintain asset lists, patches, and updates
While this should go without saying, cyber crime prevention involves keeping your company's hardware, software, and digital assets upwards to engagement through proper IT security asset management. A very easy and mutual style for hackers to get through a company's defenses is to just take advantage of security gaps that exist due to outdated or unpatched It infrastructure and software. While zero-solar day vulnerabilities — such as a Windows x cyber vulnerability for Microsoft Edge web browser users — could enable threat actors to take advantage of weaknesses that are unknown to manufacturers, the vulnerabilities they practice know well-nigh are ones that companies will often issue updates or patches to ready.

An equally important responsibleness is ensuring you lot maintain an upwards-to-appointment inventory list of all hardware, software, information, and security certificates and then you know exactly what is on your networks, servers, and other IT systems. Keeping an up-to-date list non only helps you stay informed near your avails, just information technology as well helps yous keep vital information at your fingertips so you aren't scrambling for data at the last minute should a cyber security issue take place. This will play a vital role in implementing whatsoever incident response plans (IRPs), IT disaster recovery plans (DRPs) and business concern continuity plans (BCPs).
How to prevent cybercrime — footstep #4: Manage SSL/TLS certs and keys for your domain(south)
When discussing how to prevent cybercrime, we'd be remiss to non mention the importance of using a secure protocol for your website in lieu of a nonsecure i. HTTPS, the secure version of hypertext transfer protocols for websites, is essential for every website regardless of content — fifty-fifty Google says so. This secure protocol is made possible through the use of SSL/TLS certificates — secure sockets layer and ship layer security — which authenticates websites and businesses and enables secure, encrypted communication through a process known as a TLS handshake.
In a nutshell, SSL/TLS certificates take three purposes:
- To authenticate your website or business concern,
- To ensure data integrity, and
- To create a secure, encrypted connectedness for content and data to transmit back-and-forth between a user's web browser and your web server(s).
Once SSL/TLS digital security certificates are installed, the certificates and encryption keys must exist managed to ensure that they remain upwardly-to-date and don't expire. While this may audio like a simple job, consider that the boilerplate number of certificates and keys per organization range in the tens of thousands, according to a survey of nearly 600 Information technology and IT security professionals past KeyFactor and the Ponemon Institute:
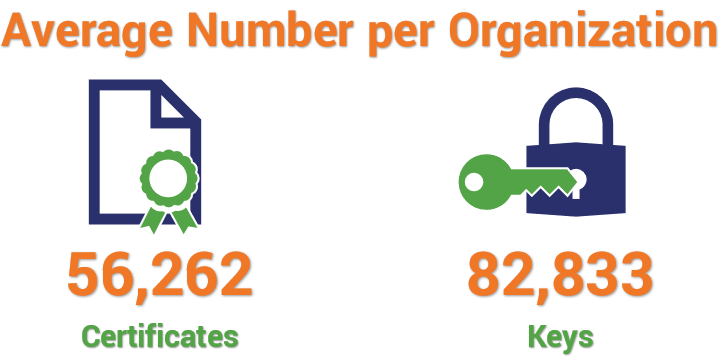
That's a lot to track continuously. This is one of many reasons why public key infrastructure (PKI) and certificate management are such of import task for every business organization, regardless of whether they rent a specialist to manage their PKI or use in-house personnel. This practise helps to avoid the problems and costs that can upshot from poor management, such as those reported in the KeyFactor/Ponemon Institute study:
| Scenario | Extrapolated Cost |
| Price of unplanned outages due to certificate expiry | $11,122,100 |
| Price of failed audits/compliance due to undocumented or poor key management | $14,411,500 |
| Cost of server certificate and primal misuse | $13,423,250 |
| Cost of Code Signing certificate and key misuse | $15,025,150 |
| Cost of CA compromise or rogue CA for MITM and/or phishing attacks | $13,219,850 |
| Total Cost | $67,201,850 |
HTTPS is considered the leading protocol and now represents 50.six% of site elements as of Apr 25, 2019, co-ordinate to W3Techs. Although we'd like for this number to be higher, information technology'due south important to consider that this statistic is up from the previous year'south standing (thirty.8%) as of April 1, 2018. The HTTP/2 protocol, which tin't exist used without encryption, as well represents 36.3% of site elements, up from 24.6% in the previously mentioned timeframes. Google even recommends HTTPS websites supporting HTTP Strict Transport Security (HSTS), which tells users' browsers to request HTTPS pages automatically (regardless of whether they type HTTP into their omnibox) to minimize the risk of delivering unsecured content.
How to forestall cybercrime — footstep #five: Train employees to place and react to threats
Do you know what the biggest vulnerability in cyber security is for about businesses? If you guessed "employees" or "employee negligence," then you are right. Employees (in house and remote) represent the near pregnant security risk to businesses and employee negligence is the leading cause of data breaches, co-ordinate to research from Shred Information technology. While I may not have a prize to offering, I can at least share some relevant insight on how to protect yourself from the numerous cyber threats that exist and seek to exploit your cyber vulnerabilities.

Cyber awareness training provides a basic agreement of cyber security best practices. Dandy training teaches employees — everyone from C-level executives to the janitorial staff — how to:
- Identify and respond to phishing and other electronic mail scams (hint: don't engage with them).
- Exercise safety internet habits (such as creating secure passwords and not using them across multiple accounts).
- Familiarize themselves with your organization'due south cyber security-related policies and bide past them.
- Recognize social networking threats.
- Safely collect, store, manage, and ship customer and company data.
- Comply with government and industry regulations.
Your employees are your company's outset line of defence force. While automated cyber security protections such as firewalls, antivirus and antimalware solutions can aid, they don't block every threat. This means that your employees need to be able to recognize and act quickly (and safely) to threats that make it through your network and other systems' defenses. They also need to know how to not create risks by treatment sensitive data and data appropriately.
Effective cyber security training for cyber law-breaking prevention is educational for both your employees and your It security staff. Though nosotros already know the way that it is educational for the onetime, the fashion that it is also educational for the latter is that it should involve regular testing likewise. This training helps info sec professionals appraise what is or is non working from the grooming so they can place areas they need to drill down on more in-depth to increase employee understanding. One example of such testing, phishing simulations, volition exist discussed in the next section.
How to prevent cybercrime — step #half-dozen: Implement email security solutions and phishing simulations
Considering the ascension in business email compromise, phishing, and other email-related concerns, the modern virtual mailbox represents a meaning area of cyber security vulnerability. Dissimilar concrete messages sent by a physical mail carrier, emails can contain a variety of threats from attachments containing malware (often Microsoft Part files such as Excel spreadsheets and Word documents) to embedded links that direct users to malicious websites.
Many businesses tend to rely on the anti-spam filters that come with arranged with their email platform or antivirus programs to protect their concern'south communications. However, at that place are additional third-party email solutions that y'all can utilise such as anti phishing platforms and electronic mail signing certificates.
Anti phishing platforms can automatically place and fifty-fifty quarantine potentially unsafe emails and so users can't engage with them. Some anti phishing solutions even provide an educational component to assistance users understand why emails are being quarantined (such every bit a sender's name non matching their electronic mail accost or signature, embedded links directing users to dangerous websites, etc.). Email signing certificates allow users to digitally sign and encrypt emails containing sensitive or confidential information to avert man-in-the-middle (MitM) attacks and eavesdropping. Past signing your emails, it allows your recipients to authenticate that you are yous and mitigates email tampering.

While putting these protections in place is exceedingly of import, you still need to take it a stride further and conduct periodic phishing simulations. This volition allow yous to test the cyber security awareness of your employees to assess how well they can use the lessons from your training in real-life scenarios. Seeing whether employees are budgeted email more judiciously or are opening every letters with wild carelessness volition help you recognize which employees are your biggest risks as well as identify new areas to address with cyber security and phishing awareness grooming.
How to forbid cybercrime — footstep #7: Monitor traffic and access to increase visibility
If you desire to keep an eye out for danger, it'due south best to continue the lights on, pay attending to everyone coming and going, and brand regular patrols. What many businesses do instead is plow off the lights, plow on the Idiot box, and ignore everything else. By always keeping their attention focused on something else and not paying attention to the traffic and things going on around them, they will miss of import cues and won't be able to observe or acquire from situations that occur.

In a nutshell, this concept summarized the importance of IT threat monitoring. This office involves continuous monitoring of the traffic, access, and denial logs on your network and other It infrastructure components such as servers and workstations. It tin involve the use of security information and event direction (SIEM) tools and intrusion detection/intrusion prevention systems (IDS/IPS) but too tin include the services of a cyber security operations middle (CSOC). A CSOC team tin provide 24/7/365 monitoring of systems and logs to ensure that threats are identified and addressed to mitigate damage. This can be particularly helpful in monitoring traffic to identify distributed denial of service (DDoS) attacks, which can upshot in a slow network, iffy connectivity, or even website downtime.
How to preclude cybercrime — pace #eight: Regularly assess and examination your systems
Vulnerability assessments, risk assessments, and penetration tests are simultaneously the best friends and annoying acquaintances of Information technology security experts everywhere. Although these terms are frequently incorrectly used interchangeably, these three methods of IT security they are related but separate functions:
- A vulnerability assessment helps to identify, assess, and prioritize any vulnerability in cyber security that may exist in your existing arrangement.
- A take a chance assessment, on the other paw, is useful for evaluating potential risks for specific tasks or events (if you did "A," then X could happen as a result).
- Lastly, penetration tests are your It security team's way of testing to see how your defenses tin be breached or compromised.
The goal with these tools is to help you understand the strengths and weaknesses of your cyber security posture. This knowledge is just as valuable as knowing the strengths and weaknesses of your enemy — in this case, hackers or insider threats. This arroyo supports the ancient wisdom of Chinese military strategist Sunday Tzu in (a translation of) his military treatise "The Fine art of War":

"If y'all know the enemy and know yourself, you need non fear the effect of a hundred battles. If you know yourself simply not the enemy, for every victory gained yous will also suffer a defeat. If you know neither the enemy nor yourself, yous volition succumb in every battle."
These tools are invaluable in terms of identifying network vulnerabilities, out-of-date software that need patching or updates, gaps in your existing cyber security defenses, and other cyber security vulnerability concerns.
How to forbid cybercrime — stride #9: Develop, implement, and enforce security policies
While analyzing, poking, and prodding your network and other Information technology systems is neat, you still demand to take it a step further and implement other protective measures in the form of cyber security policies. In the world of IT security, there are many types of security-related policies to choose from such as computer use policies, password policies, remote admission policies, email/communication policies — the list goes on and on. Each of these policies has its own benefits and merits that should be considered.

Access management and an admission command policy are too extremely of import. Regularly review who has access to what systems, data, or information to ensure that you're non leaving your business open to set on or insider threats. Limit employee access through a policy of to the lowest degree privilege (POLP) to ensure that each employee simply has access to the tools and information their task necessitates. This will help to limit your potential risk by reducing the number of people who have admission to your most valuable data. NIST offers a valuable resources that links to several of their access control policy and implementation guides that you lot tin can review for additional information.
Just call back, yet, that a policy is only as practiced equally its enforcement. If you lot put policies into effect merely never follow up or enforce them, then they are essentially useless documents that serve no purpose. Be sure to enforce each of your security policies to ensure that your business is getting the near protection possible.
Final thoughts
Considering many (though not all) cybercrimes involve cyber security attacks and exploiting known and zero-mean solar day vulnerabilities, implementing this combination of tactics, policies, and processes will help to significantly strengthen your cyber security posture — and your level of cyber resilience along with it.
Hopefully, it likewise means that the vocal lyrics we shared with yous at the beginning of this article volition change and be aimed at prospective hackers and threat actors:

Every malware you make
Every piece of information you take
Every electronic mail you fake
Every website you scrape
I won't fall for you…
(Or your cyber attack tactics).
What boosted recommendations or best practices practise y'all have on the topic of how to prevent cybercrime?
Source: https://www.thesslstore.com/blog/how-to-prevent-cybercrime-9-helpful-tips/
0 Response to "what policies should be in place to help reduce risk of cybercrime?"
Post a Comment